Attribute-Based Access Control (ABAC) – Access rights based on attributes
Attribute-Based Access Control (ABAC) is playing an increasingly important role in assigning user rights in on-premises Active Directory environments, but also in the cloud with Entra ID. The article explains how ABAC works and what to consider, including how it compares to Role-Based Access Control (RBAC).
Index
What does Attribute-Based Access Control (ABAC) mean in the context of IAM?
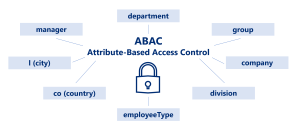
First of all, ABAC is one of the most important ways to control Identity and Access Management (IAM) in networks. In contrast to specific roles, such as Role Based Access Management (RBAC), ABAC focuses on the attributes of the controlled objects or users. This naturally offers extreme flexibility and ultimately also more security in Identity and Access Management.
The attributes used include data that uniquely identifies users and their current status. This can be
- name,
- position,
- department,
- location,
- positioning in the hierarchical structure
and other attributes, which can be used for the assignment of authorizations.
With ABAC, accounts for new users are set up very quickly and at the same time with the highest level of security. In addition, the access rights of the users always remain up to date. Only the attributes need to be updated. The rest happens automatically.
What are the benefits of ABAC for access management?
ABAC is a flexible and fine-grained access control system. It is capable of covering a wide range of use cases that are difficult to handle with traditional role-based access control (RBAC) systems.
An IAM software maps rules based on attribute values:
- These can be single attribute values (e.g. department = “IT”) or combinations (e.g. location = “Hamburg” and business unit = “Cargo” and position = “Manager”).
Based on the associated attributes, the systems finally determine which rules and permissions apply to a user. The rules granularly control the rights of the users based on the defined attributes.
- For example, all users with the “Sales” attribute under “Department” in Active Directory are automatically granted access to specific file shares for Sales, to SharePoint pages, or access to areas of the ERP system. The system recognizes the attributes and can automatically create an email mailbox in Exchange or Exchange Online. Likewise, it is possible to automatically add the user to specific distribution groups in Exchange.
Intelligent IAM software, such as the IDM-Portal, works differently than conventional IAM systems. Since the IDM-Portal works without its own database, attribute changes are implemented via the portal directly in Active Directory and thus permissions are automatically linked.
Specifically: If one changes the location of a user, the changes are set in the IDM-Portal and applied directly in the source system, the Active Directory. At the same time, the rights dependent on the location are automatically changed via ABAC. In addition to ABAC, the IDM-Portal also uses role-based IAM delegation – in other words, a combination of the two methods.
Why is ABAC so valuable in Identity Management?
Here are some reasons why ABAC is valuable to organizations:
Flexibility : With ABAC, organizations define access rules based on a variety of attributes. This allows greater flexibility and fine granularity in defining access rules compared to RBAC systems, which are often limited to a rigid structure of roles and permissions.
Full automation: When applying ABAC, authorizations are assigned fully automatically. Through special filter settings and linked attributes processes start, which implement the permissions automatically (e.g. during user creation). DynamicGroup for AD, also part of the IDM-Portal EnterpriseEdition, specializes in fine-grained linked filters for creating dynamic permission groups.
Scalability: With ABAC, organizations create rule sets that are applicable to a large number of users, roles, and resources without exponentially increasing complexity. This makes ABAC particularly suitable for larger organizations and systems.
Adaptability: Because ABAC is based on attribute-based rules, it can be adapted to changes in the business environment simply by changing the attributes or the rules applied to them. This is especially important in a rapidly changing business environment where role-based systems can struggle to keep pace.
Security: ABAC helps improve data security by restricting access to sensitive data based on specific, attribute-based rules. This reduces the risk of data breaches and facilitates compliance with data protection regulations.
Compliance: ABAC helps companies meet compliance requirements by restricting access to specific data or systems based on specific, feature-based rules. This is particularly useful in highly regulated sectors or in situations where certain data may only be accessible to specific individuals or under specific conditions.
A prerequisite for ABAC is the existence of good data quality. Without well-maintained and standardized data, no rules can be defined to automatically assign rights
In summary, ABAC provides a flexible, fine-grained and adaptable access control solution. It improves both data security and compliance for enterprises.
What does Role-Based Access Control (RBAC) mean?
RBAC is also a successful model for managing and controlling access to resources on a network. It is a standalone concept for access management and is used differently in some cases than ABAC.
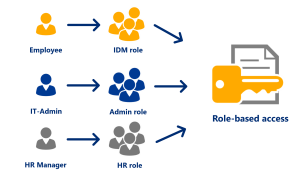
With role-based access control (RBAC), users are assigned to a specific role and given the permissions that have been approved for that role.
- For example, a user with the administrator role is assigned full permissions (read, edit, delete), while a standard user is assigned a role with limited permissions (e.g., only limited read permissions).
Roles can be configured in any number – as granular as an organization needs. However, with an increasing number of roles, administration becomes confusing.
In practice, it often turns out that a combination of both concepts – ABAC and RBAC – leads to the best solution.
What are the advantages of RBAC compared to ABAC?
Here are some advantages that RBAC offers compared to ABAC:
Simplicity and understandability: A major advantage of RBAC is its simplicity and understandability. With RBAC, permissions are granted based on defined roles, which is intuitive and easy to understand in many organizations. Each role represents a specific function within the organization and has specific permissions. This makes it easy to visualize and understand access rights.
Easy management: RBAC simplifies the management of access rights, especially in medium-sized organizations. Users are assigned to an already defined role and the access rights behind it are automatically transferred. Changing the access rights of a role affects all users assigned to that role. RBAC is often used for manual or semi-automatic administration.
Consistency: Because permissions are granted based on roles rather than on an individual basis, RBAC provides greater consistency of permissions. All users with the same role have the same access rights, ensuring consistent enforcement of security policies.
Minimal permissions: RBAC facilitates the enforcement of the principle of minimal permissions, also known as “least privilege”. Each user has only the permissions they need for their role, reducing the attack surface for malicious actors.
Cost-effectiveness: RBAC can be more cost-effective than ABAC, especially in terms of implementation and management. While ABAC offers more flexibility, this flexibility can also lead to more complexity, requiring more time and resources for implementation and maintenance.
Compared to ABAC, RBAC offers a simpler and possibly less expensive access control solution that is sufficient in many situations. It offers a different kind of flexibility than ABAC. ABAC may actually add unnecessary complexity in some cases. This is why RBAC is often the preferred solution for mid-sized organizations, while ABAC (or a combination of both concepts) is better suited for larger and more complex enterprise structures.
What are the differences between ABAC and RBAC?
Attribute-Based Access Control and Role-Based Access Control are two different methods for controlling access to resources in a system or network. Both approaches have their strengths and weaknesses and are suitable for different use cases.
Here are some of the key differences between ABAC and RBAC in an overview:
| ABAC | RBAC | |
| Basis for access to resources or permissions | the attributes of the user or the respective object | the respective role of a user (e.g. organizational) |
| Type of authorization management | granular | less differentiated |
| Permissions | are assigned to (multiple) attributes | are assigned to (multiple) roles |
| Total number of authorizations to be sensibly managed | very high number of possible combinations of attribute values; can manage large number of permissions | Users can have many roles, but usually less than attribute combinations |
| Granularity | very high due to the large number of attributes | less high due to the lower number of roles |
| Degree of automation | Full automation possible | Manual administration or semi-automation |
| Suitable for | large, complex IT systems | IT systems of medium size |
| Complexity (Implementation and administration) | high to very high | normal to high |
| Scalability | more scalable in large and complex structures | depending on the required number of roles (exponential increase) |
Ultimately, ABAC and RBAC represent different approaches to access control that vary in suitability depending on an organization’s needs.
Are there any advantages or disadvantages to using ABAC and RBAC?
Identity and access management (IAM) administration is more flexible and granular with ABAC than with RBAC. On the other hand, administration is somewhat more complex.
RBAC roles are often defined very narrowly. This often leads to users receiving more rights than they actually need as a result of their role assignment. As a result, the security of the environment suffers unnecessarily. In comparison, ABAC offers optimal authorization management that provides maximum control and thus maximum security.
Once the attributes are assigned, ongoing management is again simpler than with RBAC. Each user is given access to the resources that are made available to him and that he needs for his work. This is, of course, easier to control with attributes. Much of the control is automated via the ABAC solution in use, for example via the IDM-Portal. Another advantage of ABAC is the improved compliance control. The automated processes in ABAC ensure that, based on the assigned attributes, all rights are always in compliance.
Granular control of access permissions with the IDM-Portal
Using ABAC in the IDM-Portal
Using IAM software solutions such as the FirstWare IDM-Portal quickly compensates for the complexity of the ABAC method.
The IDM-Portal provides an admin-friendly way to use ABAC in the enterprise. In the IDM-Portal, when ABAC is used, an attribute value is associated with an authorization.
- For example, department authorizations can be controlled via the selection of the department or via “UserType:” with the values “internal” or “external”. The status of a user also plays a role here. If a user goes on parental leave, for example, his account automatically loses various permissions.
Furthermore, not only one attribute can be used to set an authorization. Also the combination of different attributes is possible:
- Company (value: Univice LTD) leads only to certain departments (values: USA departments). The attribute Functional Role (value: Manager) then leads in combination of this to an authorization: OG-US Sales Manager.
With RBAC, these combination possibilities would lead to a long selection list, and with ABAC, combinations would lead to a targeted authorization. In both cases, the underlying authorization must still be defined.
DynamicGroup and DynamicSync also support ABAC
When using DynamicGroup for AD and DynamicSync for Entra ID, ABAC is also used. In this case, user account attribute maintenance is done in the IDM-Portal. DynamicGroup then takes care of adding the users to the corresponding dynamic AD groups based on these attributes. DynamicSync enables the distribution and maintenance of M365 groups.
Summary
ABAC is a useful approach to define access rights in a very detailed way based on attributes used in directories, such as Active Directory. However, it requires administrators who love details and have the time and patience to develop a well thought-out concept for assigning rights via attributes.
In general, it is advisable to check whether a role-based approach (RBAC) is sufficient for a company’s requirements. This is our recommendation: as a first step, assess the complexity of the requirements and check feasibility. The larger a company is and the more complex the management of identities and access rights becomes, a mixed approach of RBAC and ABAC may be the right way to go.
The FirstWare IDM-Portal handles the complex assignment of permissions of both approaches and makes it manageable in a user-friendly application.
We will be happy to advise you on how to implement ABAC and RBAC methods in practice. As experts in the field of identity & access management for on-premises and cloud environments, we know what matters when it comes to user and authorization management. Contact our friendly team.